Table of Contents
Below is an overview of the main functions. More details about the product can also be found at www.migRaven.com.
Data separation (data retention / archiving)
The migRaven.24 / 7 Data Retention is an innovative way of archiving obsolete data.
The primary goal is automatic optimization of directory structures and the Saving storage costs.
The optimization is achieved by moving the "obsolete" data further down in the directory tree. The relevant data remains in place. Directories that no longer contain files are replaced by migRaven away. This makes the directory tree lean and clear.
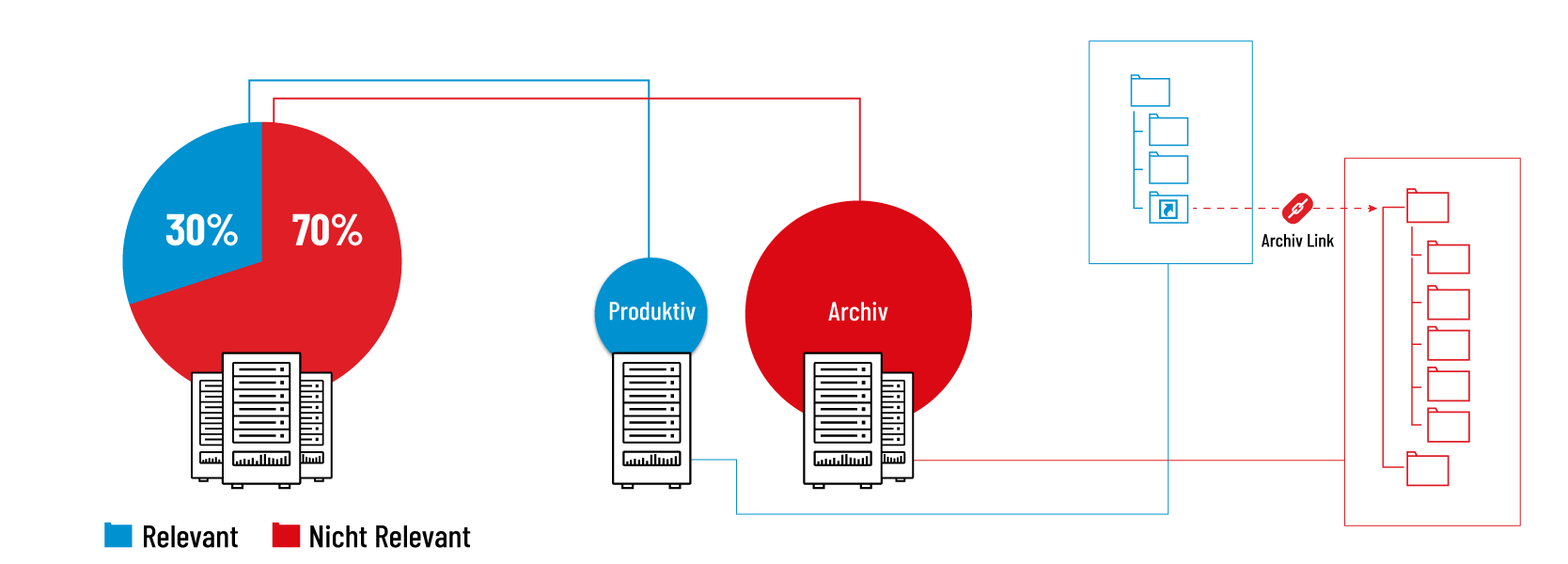
With one-time or regular archiving processes, no residues are left in the productive system. This prevents the amount of data on the file server from increasing and even prevents this volume of data from decreasing. The directory structure is also cleaned up accordingly by deleting empty directories.
The big advantage of our solution is the division of the data into an active and passive memory area. This improves the overview for the user of the really important files and thus enables faster access with less frustration.
| Initial Situation | After optimization |
|---|---|
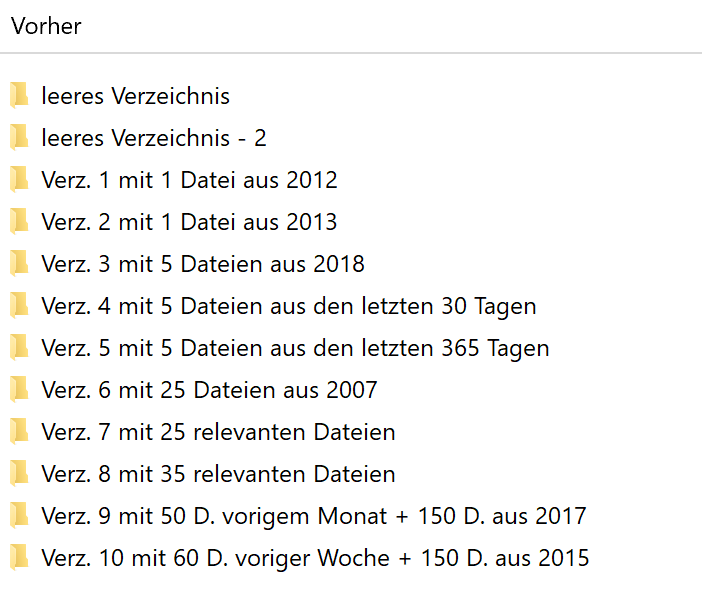 | 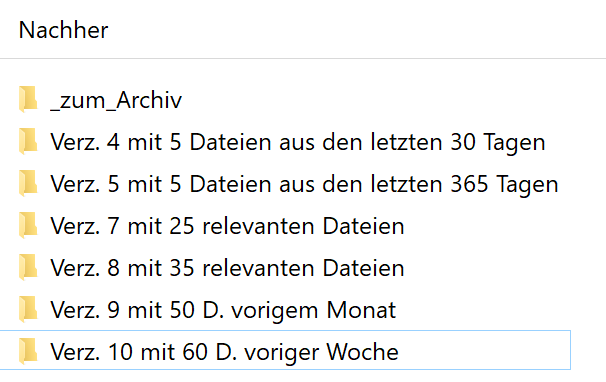 |
Recommended articles:
All articles related to configuring data retention
All articles in the category: Data Retention – Archiving
Template based directory creation (User/Folder Self Service)
If employees from different departments work together on a project, the request for a suitable file storage quickly becomes loud. This shelf must of course also meet all security requirements.
The hope that the users will delete the data that is stored there is also rarely confirmed.
migRaven.24 / 7 User / Folder Self Service meets the requirements for security and data management.
The employees can independently create directories in a web interface or the desktop client and determine who can access the directory. Since each of these directory attachments is based on a template previously configured by the administrator, potential wild growth is prevented from the outset.
In addition, the administrator has the option of configuring run times for created directories, after which the directories are automatically deleted.
Recommended articles:
All articles about configuring directory creation (Web Client)
All articles about directory creation via template (Web Client)
Directories in the desktop client draw up
Best Practice/ Least Privilege Authorization Management
Authorization management in Microsoft file server structures is quite complex and error-prone if you administrate it with on-board tools. migRaven provides the necessary tools to be able to manage authorizations in the simplest way. takes over migRaven complete the administration of all necessary authorization groups that are necessary for this.
The high flexibility also allows management in complex domains Forrests.
The best thing is that it is optimized for use by inexperienced user groups. More than 15 years of experience have gone into the implementation in order to support everyone as optimally as possible.
there is more here: Authorization management of existing directories
Instructions for users & data owners:
By Folder Self Service Employees manage their exchange and project directories themselves. Similarly, all data owners can use the preconfigured ones Data Retention Policies for the storage of old data.
Because these functions are to be used heavily by users, we also supply the following two manuals for the departments.
Problem explained in the video: That's why you need migRaven.24/7
31.05.2019 | 04: 36 minutes | Presentator: Thomas Gomell


1 comment
Das gefällt mir.