1. description
The question of the use of shares is always relevant in migrations. If you switch off a share or migrate to a new server, you should know whether all eventualities have been taken into account.
The event can provide information as to whether this is the case.
Here creates the EventReader of aikux.com Remedy.
Its main goals are:
- Determine the use of each individual share / directory
- Identify the contact person / data owner of the shares / directories.
- Identify applications from which the share is accessed.
- Find system accounts that access data / shares.
- Detect applications that are currently configured incorrectly. Possibly. a user account is set up instead of a service account.
The EventReader can be used from Windows Server 2008 upwards and EMC.
Summary
Auditing policies are enabled on the unknown shares, which generate Windows security events with the ID 5145.
These include the following information that is relevant to the above goals:
- Who: Which account has accessed
- Where: Which computer (host name) was accessed
- When: The time of access
- what: Which file was accessed
The aikux.com EventReader retrieves the events remotely from the EventViewer of the file server to be examined and consolidates the results via a hash table in just a few minutes. This means that each combination occurs only once in the result table.
Optionally, the file names can be included in the analysis, but this increases the result set.
If you only need the accounts and hostnames, you can switch off the capture of the file name either.
Requirements
The EventReader outputs the events written by Windows in a CSV file.
Prerequisite, however, is that Windows also writes the desired events.
This requires the use of Group Policy Editor to enable some system monitoring policies.
In addition, the monitoring must be activated on all shares to be examined.
Then we have to give Windows some time to log sufficient events for an evaluation. Usually 3-5 days are sufficient for this.
The EventReader requires the .NET Framework version 4.5.
2. Set up surveillance
2.1. Set the object to be monitored
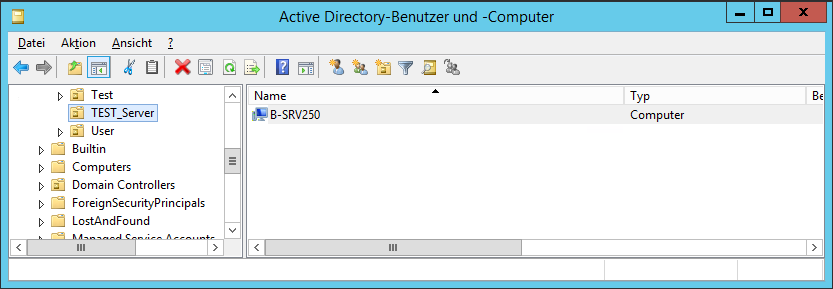
First, we create an OU in our Active Directory (here: TEST server) and move the server to be monitored (here: B-SRV250) into it.
Note:
If your server OU is linked to other important GPOs, it is recommended to create a new sub-OU and move the file server (s) to be monitored there. This ensures that the servers still receive the required settings from Group Policy.
2.2. Create a GPO
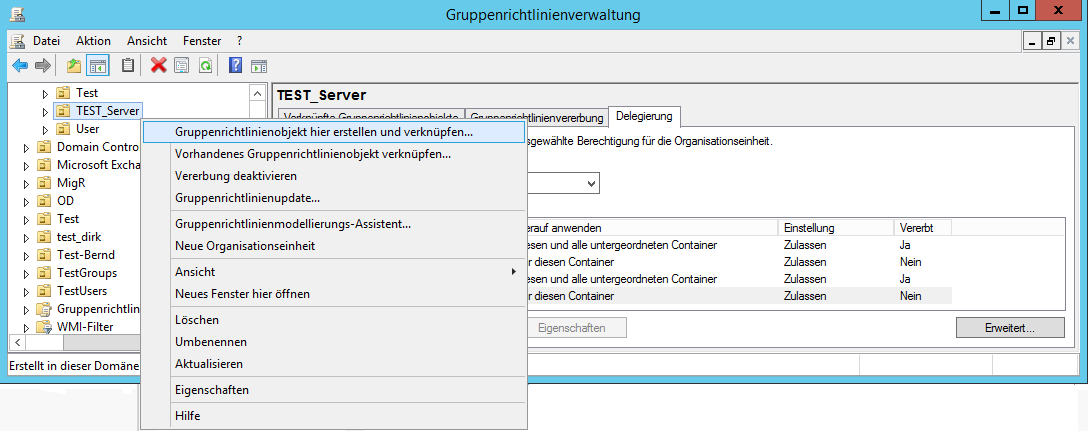
We start the group policy management (gpmc.msc) and navigate to the previously defined OU. Via the context menu we call the function "Create and link group policy object here ..." and give the new GPO a meaningful name, eg "TEMPLATE_Fileshare-Auditing".
2.3. Edit GPO
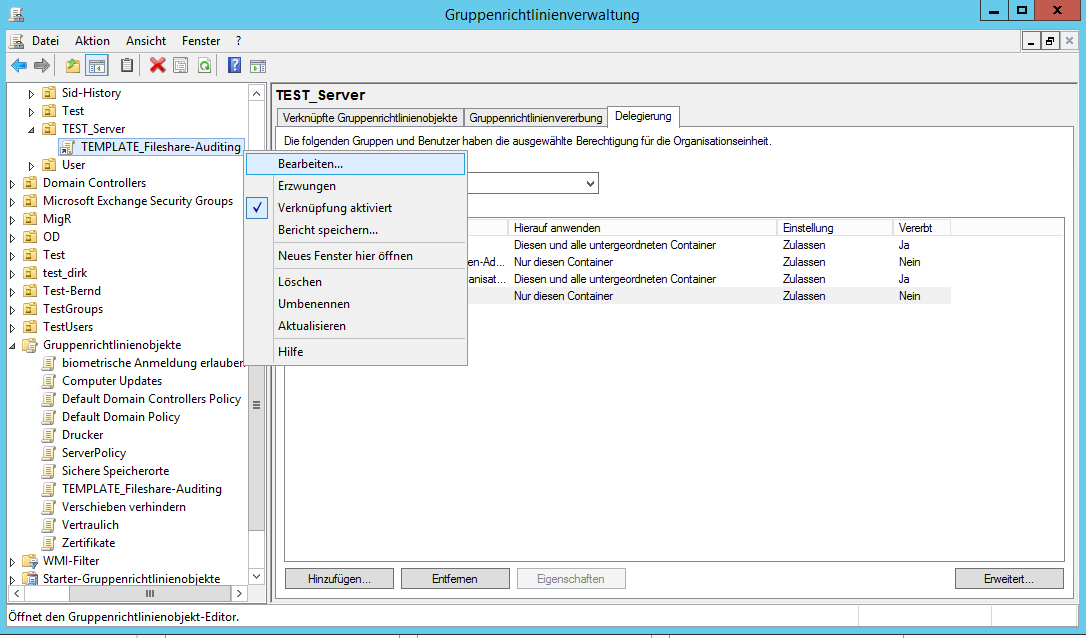
Via the context menu of the previously created group policy, we enter the edit mode.
2.4. Audit Policy
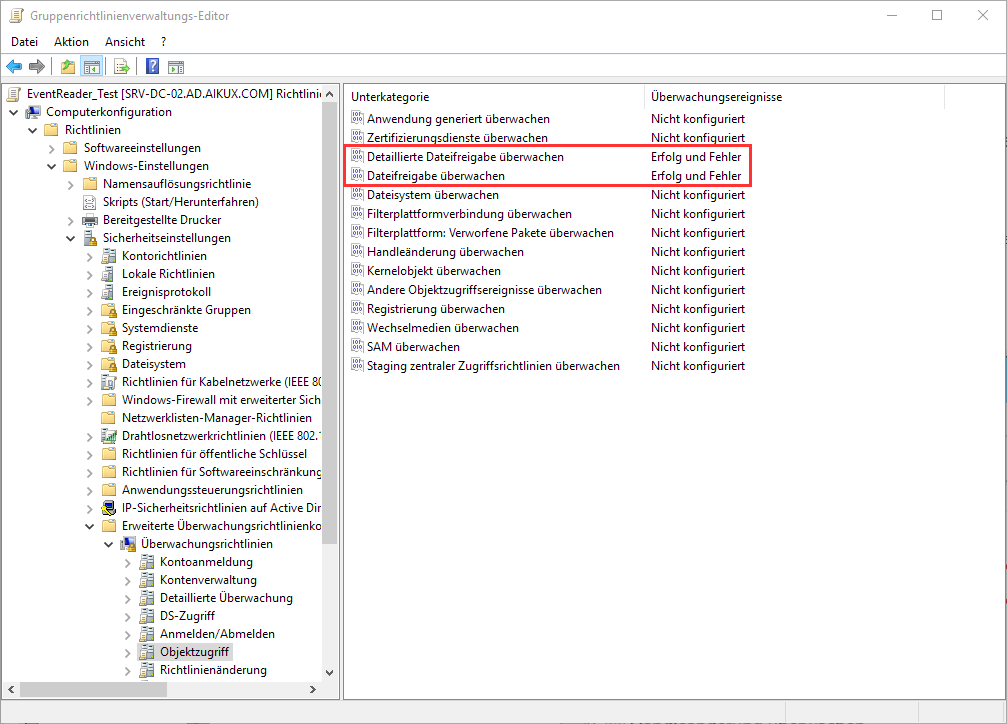
In the Group Policy Management Editor, we must make the following monitoring settings.
To do this, the settings "Monitor file sharing" and "Monitor detailed file sharing" must be activated.
These log events with the Event ID 5145 when a file or folder is accessed in a shared folder.
Location: Computer Configuration> Policies> Windows Settings> Security Settings> Advanced Audit Policy Configuration> Audit Policies
Object Access Object Access Monitor detailed file sharing - Success / Failure Audit Detailed File Share - Success / Failure Monitor file sharing - Success / Failure Audit File Share - Success / Failure
2.5. Further guidelines
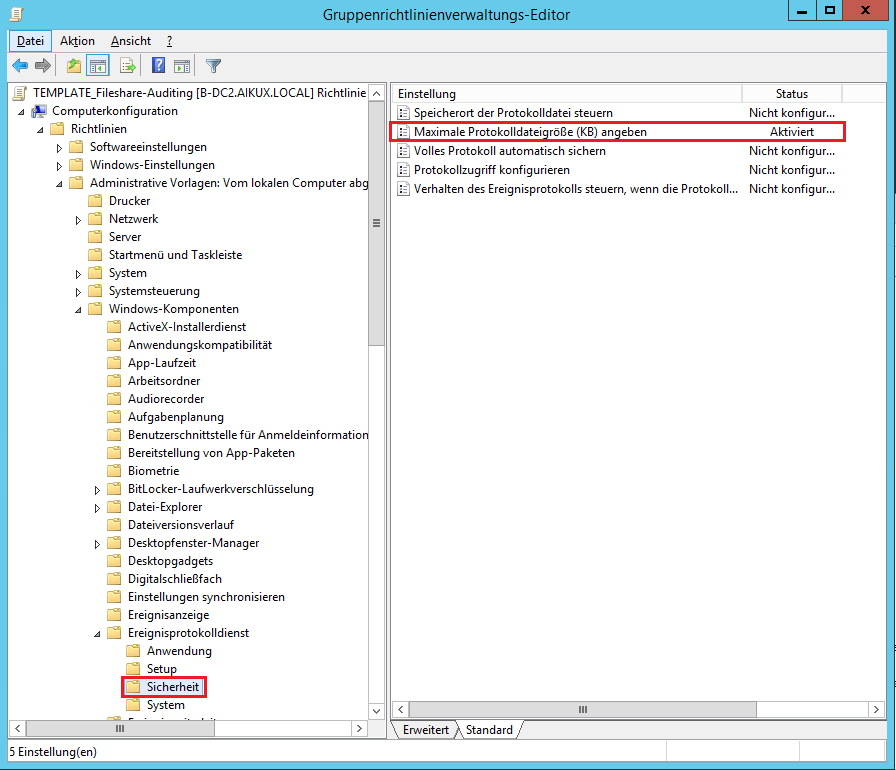
Log File Size
Since the settings made significantly increase the number of written events, the size of the log files must also be increased. It must be adjusted here the size of the log file security. There, the collected events are stored with the ID 5145.
Location: Computer Configuration> Administrative Templates> Windows Components> Event Log Service> Security
Specify the maximum log file size (KB) Specify the maximum log file size (KB) (default value is 20 MB)
We recommend that you specify the largest possible value for the log file. Mind. 10GB, better 25 GB.
The size depends on how much space is available on the C partition (default location of the Eventviewer is always:% SystemRoot% \ System32 \ Winevt \ Logs \ Security.evtx) of the system to be examined.
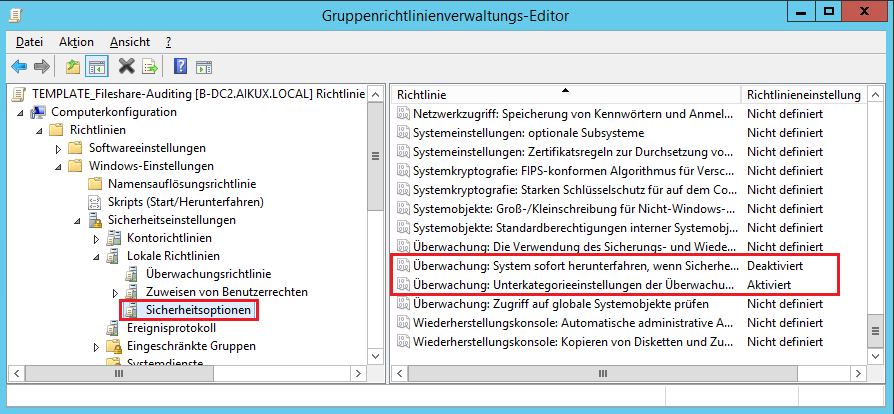
Of course, once the log file reaches its maximum size, the server should not shut down immediately. To prevent this, the following setting must be checked.
Location: Computer Configuration> Windows Settings> Security Settings> Local Policies> Security Options
Monitoring: Shut down the system immediately if security checks cannot be logged. - Deactivated audit: Shut down system immediately if unable to log security audits. - Disabled
It should also be ensured that the monitoring guidelines are enforced down to the lowest categories.
Location: Computer Configuration> Windows Settings> Security Settings> Local Policies> Security Options
Monitoring: Enforce monitoring policy subcategory settings ... to override monitoring policy category settings. - Enables audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings. - Enabled
2.6. Activation of the release monitoring on the file server
After the policy has been fully configured, it is necessary to enable the monitoring on the shares of the file server.
To do this, in the properties of the folder where the share is configured, go to System> Advanced> Monitoring the following configuration will be set up:
Principal: Everyone access: Full access Apply to: This folder, sub-folder and files
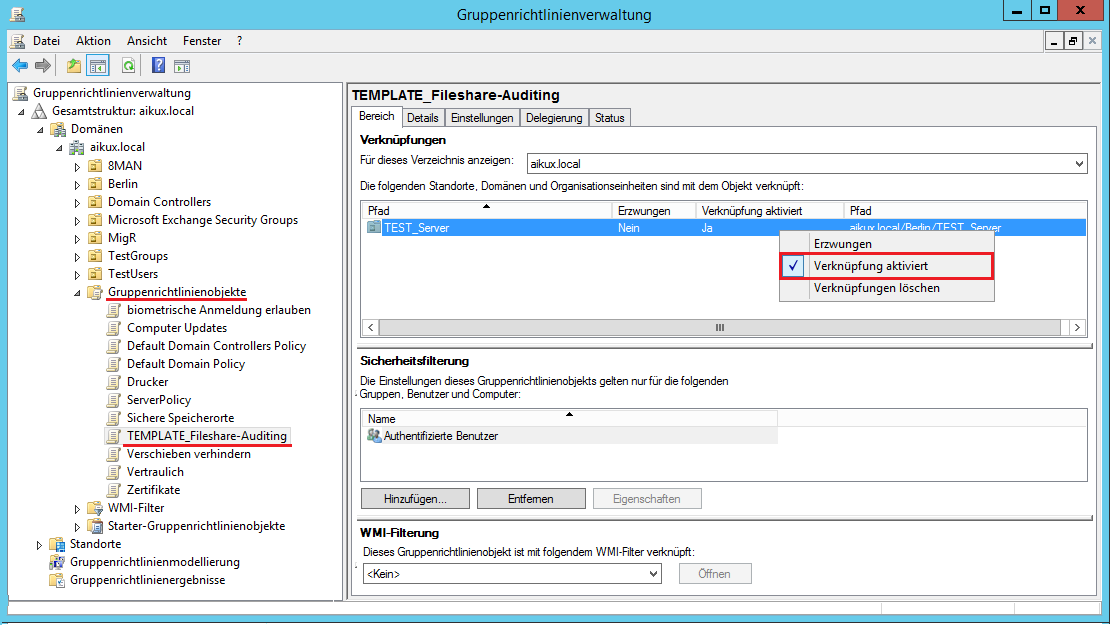
2.7. Activation of the guidelines
After all preparations have been made, the policy can be activated.
As a rule, every 90 minutes on each domain computer updates the policies in the background.
A manual exclamation of gpupdate / force via Windows command line enforces the settings immediately.
If this is not enough and no events are recorded with the ID 5145, the server must be restarted.
However, this should ideally be done in a maintenance window, or at least previously announced to the users.
When using a file-based backup, keep in mind that the change to the SACL will cause a full backup in case of doubt.
3. event Reader
The EventReader outputs the events written by Windows in a CSV file for the number of days you have left.
The evaluated events with the ID 5145 are available from Windows Server 2008.
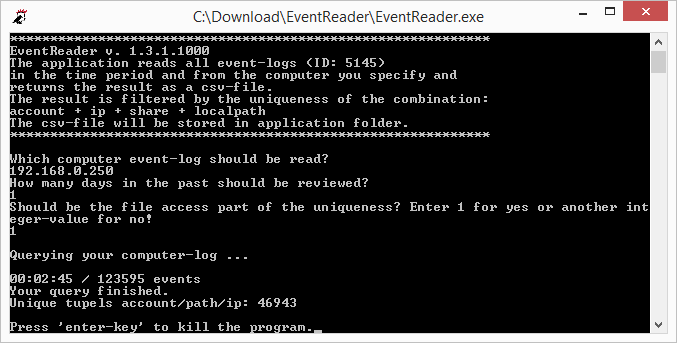
3.1. The input
The following inputs are required in the EventReader:
- the server name to be read or its IP address
- the number of days we want to look at
- Output amount: “1” for a detailed output, another number for a shortened output
3.2. The output
The data is output to a CSV file and stored in the folder from where the EventReader was started.
It contains 5 columns
- Username
- IP address of the user
- Share that was accessed
- directory name
- Exact directory and file name accessed
Note:
The shortened output misses the last column and removes the duplicates.
4. Disable the monitoring
After the events have been written to the CSV file by the EventReader for further evaluation, the previously created GPO can be deactivated.
For this it is sufficient, via the context menu of the policy in the group policy editor
- to break the link to the OU
- disable the GPO.
In addition, the monitoring must be deactivated again on the examined shared folders. Simply remove the entry as in section 2.6.