Table of Contents
The prerequisite for configuring the best practice authorization management is that you migRaven.24/7 access management have licensed.
Requirements for configuration:
Licensing of the migRaven.24/7 access management
Clarity about the Authorization strategy, for example AGDLP or AGGP.
An OU in your Active Directory where the AD Scan Service Account Can create authorization groups.
A naming convention for naming the permission groups.
Once the preparations have been completely completed, you can activate the best practice authorization management.
Please make sure that you configure at least account blacklisting in the blacklist tool immediately after activating the best practice authorization management! Setting up AC account filters: blacklist and whitelist for permission management
Best practice permission management configuration
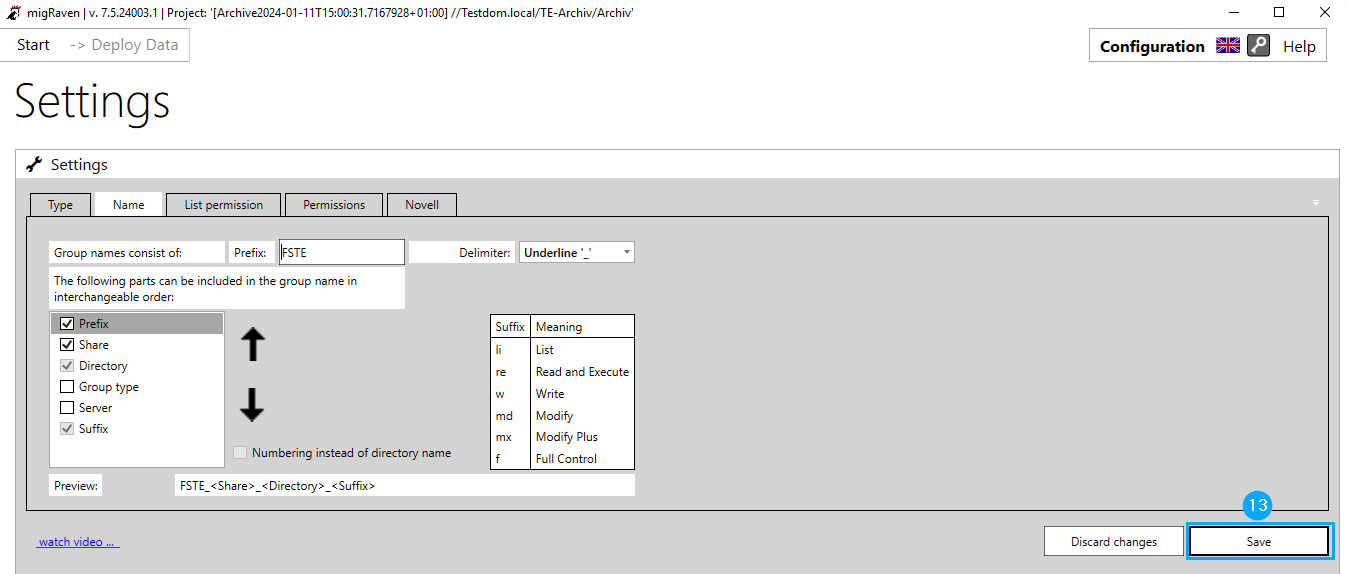
Open the configuration context menu migRaven Admin Client (1) and select the Settings menu item (2).
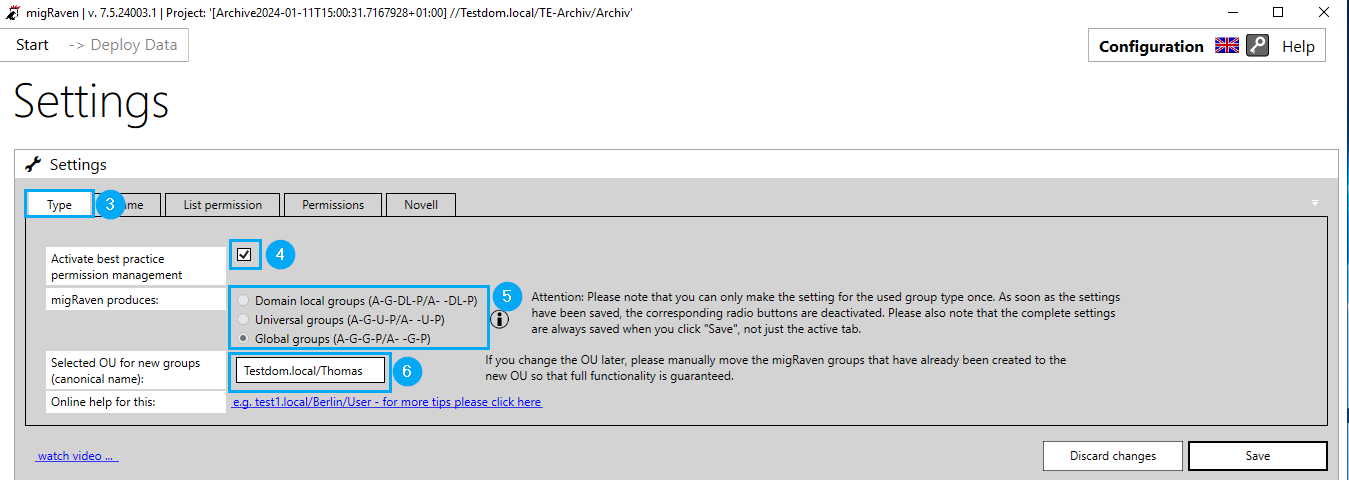
Under the Type tab (3), activate the best practice authorization management (4), select the authorization strategy (5) that you have chosen and enter the canonical name of the organizational unit (6) of your Active Directory in which migRaven.24/7 should create the authorization groups.
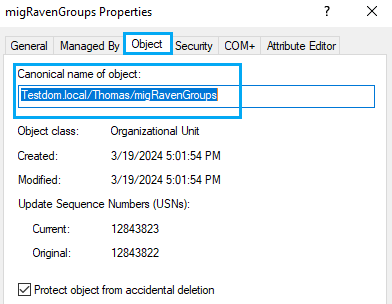
You can determine the canonical name of the OU via AD by activating the Advanced Features under View, right-clicking on the OU and going to the Object tab under Properties and copying the name there.
Please note that you cannot change the authorization strategy again after saving.
Then switch to the Name tab (7). Here you configure the naming convention of the authorization groups migRaven.24/7 will generate. Set your prefix (8), choose a separator (9), and select the components from the list that will become part of the authorization group name (10). You can use the arrows to move the group name components to a position of your choice (11).
At the end of the window you will have a preview available (12).
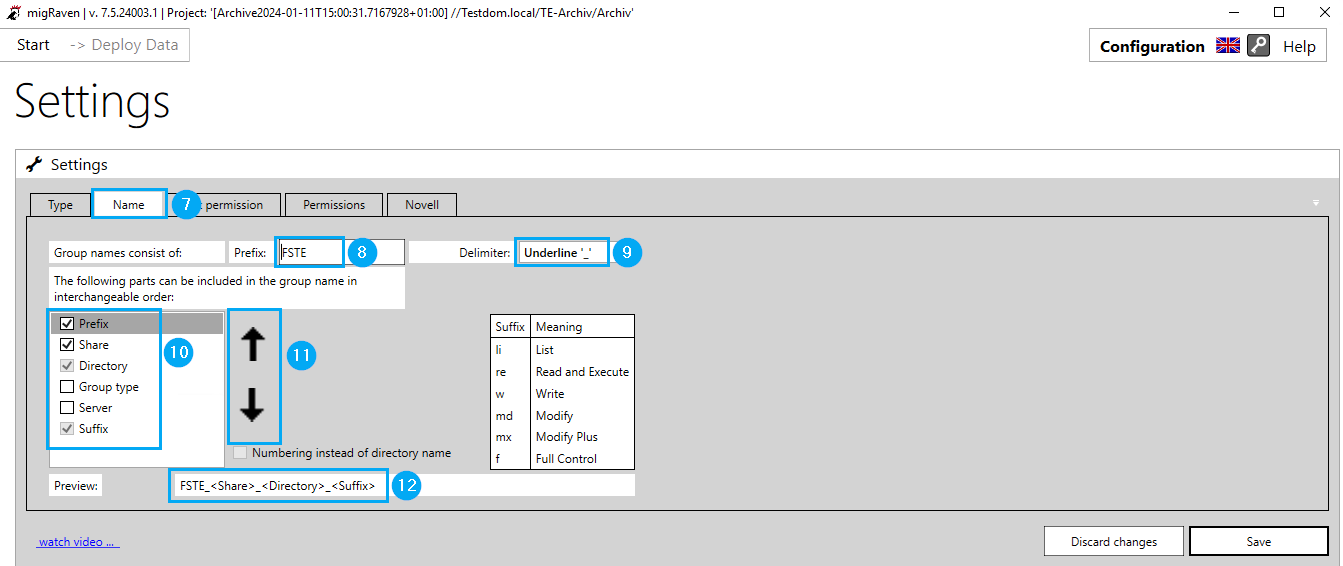
The other tabs are not relevant for activating the best practice authorization management.
Finally confirm your configuration with Save (13).
Please remember to configure account blacklisting immediately after saving! Setting up AC account filters: blacklist and whitelist for permission management
migRaven.24/7 manages all permission groups for you! You don't need to worry about it in the future.
From migRaven.24/7 Read inventory lists can, if licensed migRaven.24/7 access management, since version 7.2.22103.1 in the migRaven.24/7 Authorization management can be taken over. Previously, permissions could only be accessed through migRaven.24/7 folder self-service created directories are managed.
All authorization groups that are necessary at the time of the authorization change are created according to the least privilege principle. So no groups are created for a right in AD if they are not necessary.
migRaven creates the groups for the authorization endpoints and all authorization groups that are required for the path to the authorization endpoint, the list authorization groups on the directories above.
More information on choosing the right group type: Best practice authorization group type in AD
Behavior when granting authorization
This function is permitted for directories up to the 3rd level. For permission management of scanned existing directories, there is a license and configured migRaven.24/7 access management, a new action button in the button overlay in the directory tree, with which the permissions on the selected directory can be managed.
After clicking on the action button (14), a sidebar opens in which you can manage the data owners (15) and permissions (16) of the directory.
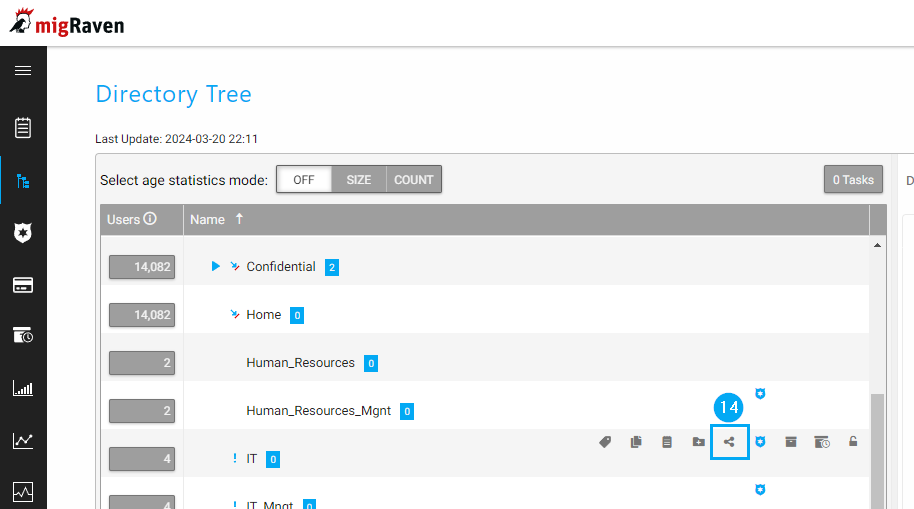
Sidebar
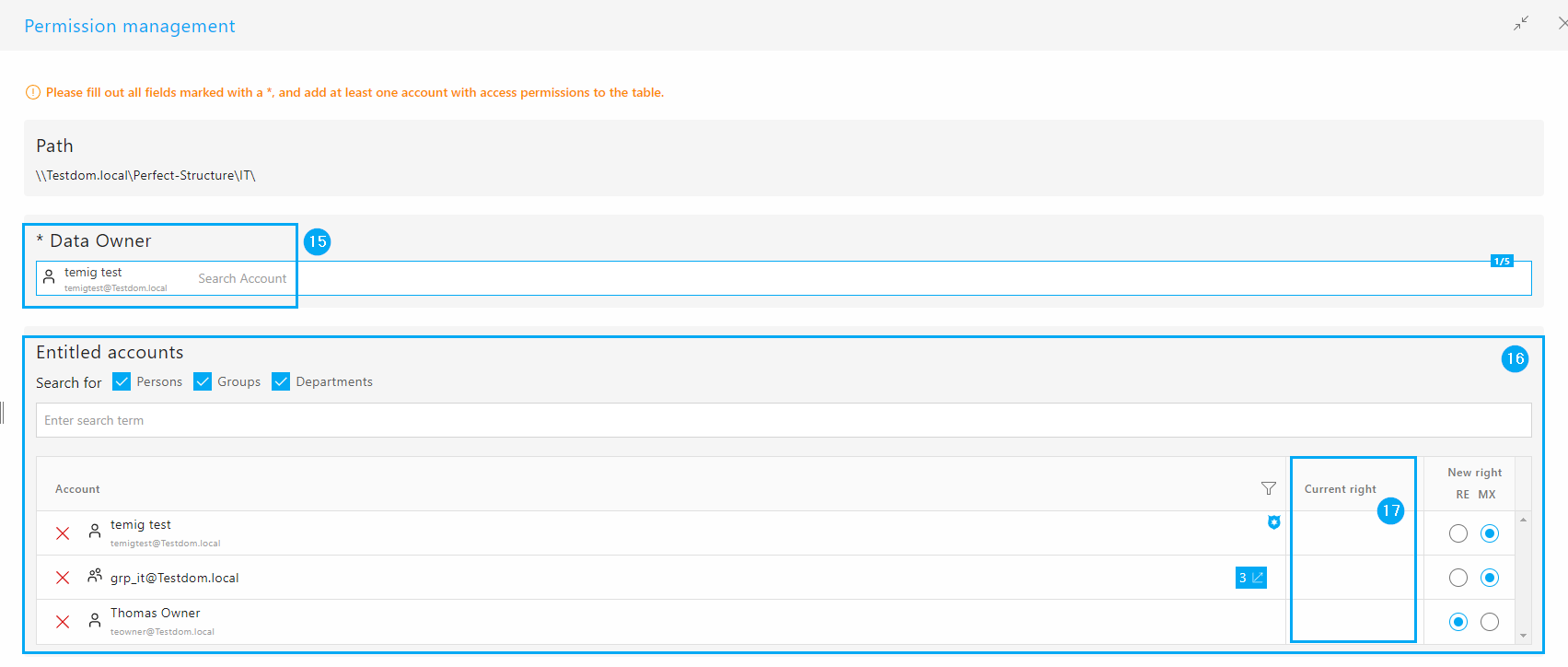
In the sidebar table “Authorized Accounts” (16), in addition to the accounts added by the user, all explicitly (not inherited) authorized user accounts in this directory are displayed. For these accounts, the current authorization (as of the last scan) is displayed in the “Current authorization” column (17). In the case of “Special Rights” you can view the individual rights in a tooltip.
The managing user, data owner, can decide here whether he wants to keep, change or remove the existing explicit permissions. User accounts can only be authorized with “Read and Execute” or “Modify Plus”. Existing explicit authorizations may not be able to be adopted 1:1, e.g. E.g. the “Change” permission for the group “grp_it..” in the screenshot above. After filling out all mandatory fields and clicking on “Apply”, the directory will be added to the authorization management migRaven.24/7 accepted. The following steps are also processed:
- Authorization groups and list groups are created in Active Directory.
- A dedicated group is created for each of the two rights “Read and Execute” and “Modify Plus”. A dedicated list group is created for each parent directory (apart from the share).
- The authorized user accounts defined in the sidebar become members of the respective authorization group.
- The authorization group(s) become a member of the list groups.
- The authorization groups are authorized on their directory with the appropriate rights.
- On the parent directories, the list groups are authorized with "List folders (Only this folder)".
- All explicit (non-inherited) permissions previously set on the directory are removed from the directory! This can result in a temporary loss of authorization until the next time the users involved log off and on, since the user accounts only know about their membership in the new authorization groups (Kerberos token) after they log on again.
In contrast to template-based directory creation, Folder Self Service, the permissions are not assigned directly, but according to best practice via dedicated permission groups. In addition, there is no runtime for adopted directories, such as: B. with exchange directories that contain migRaven.24/7 can be created.
Blacklists can be defined to protect existing permissions that cannot be removed. More on this.
Role Designer settings
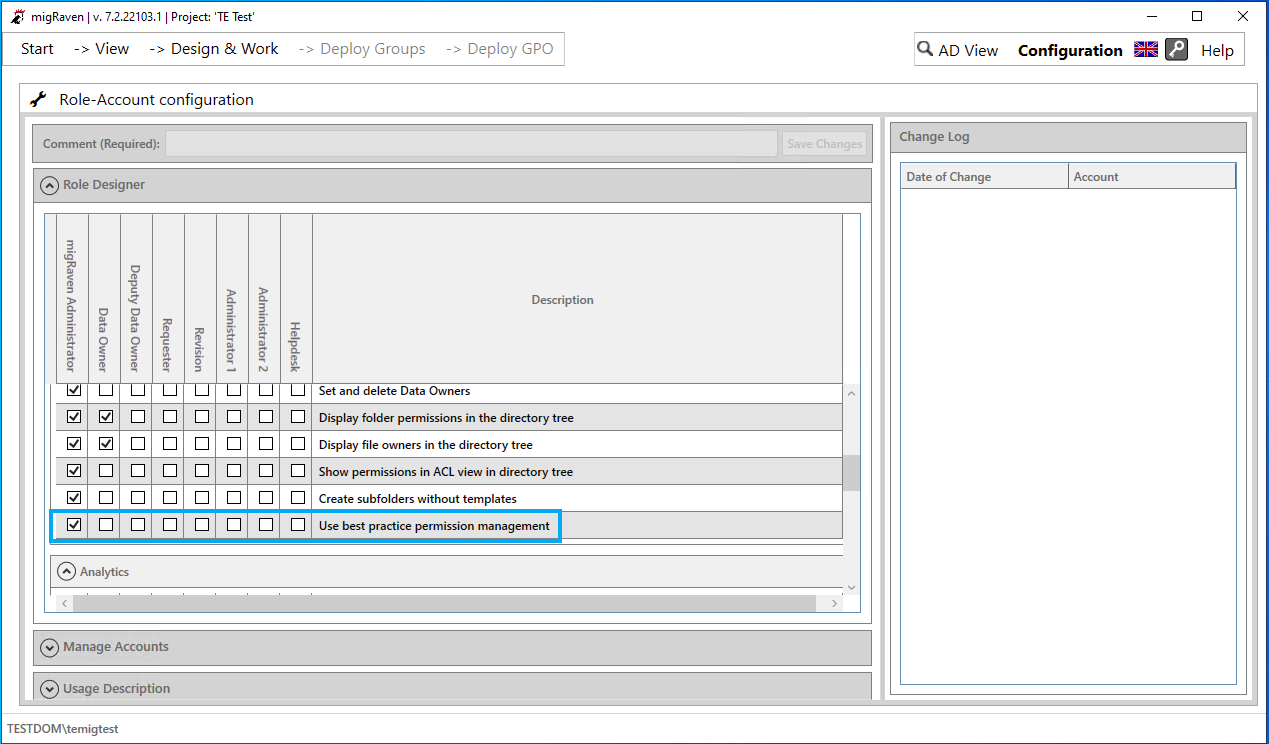
In addition, an entry in the role designer can be used to control which roles are allowed to use the best practice authorization management: “Use best practice authorization management”. This entry is standard for migRaven Administrators enabled and can be enabled or disabled for each role, assigning users to roles.
You can find other important information about the authorization groups via:

